Security architecture
This section presents the details of the SoftExpert Suite security architecture. See the diagram below:
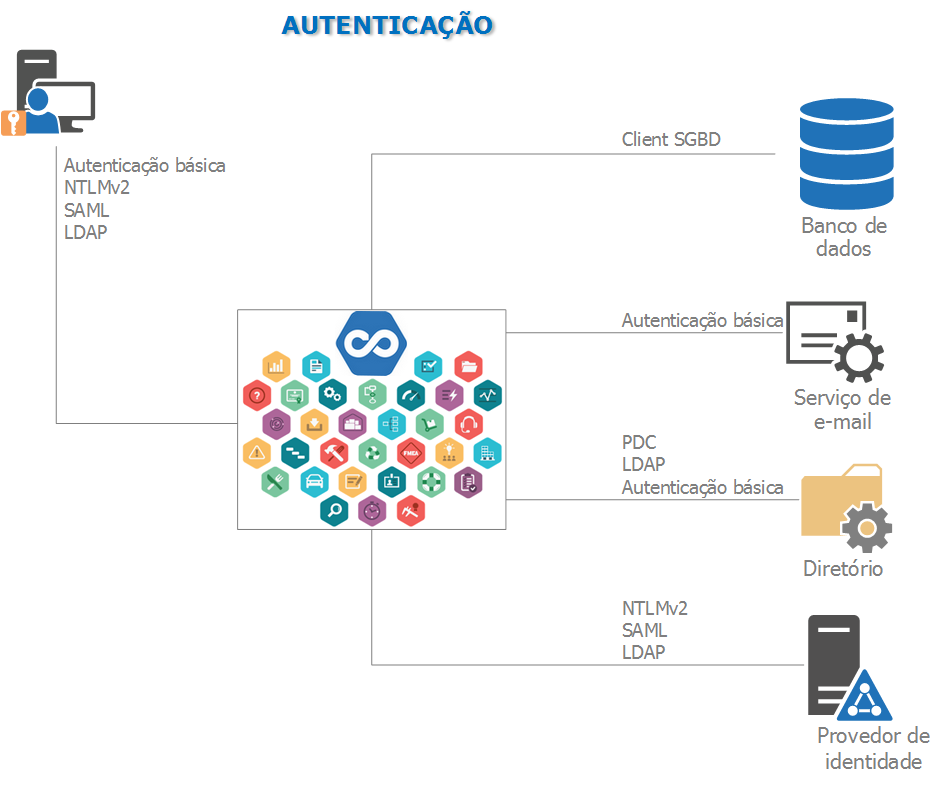
Figure 7 - SE Suite security architecture
Version 2.2 requires the use of HTTPS to increase the security while the solution is being used. We suggest the use of a valid digital certificate, issued by certifying authorities (Verisign, Certisign, Thawte, etc.). If the organization has no available valid digital certificate, a self-signed certificate may be generated (IIS or Nginx); however, security warnings may be issued to the users while using SoftExpert Suite. Refer to the SoftExpert Suite - Installation guide document to check the configuration of certificates.
This section contains the following topics:
User access
For the users on the workstations to have access to SoftExpert Suite, they need to be authenticated. For that, SoftExpert Suite makes available the following authentication methods:
- User and password: Passwords and users are stored in the database using encryption through a SoftExpert Suite algorithm added to the SHA-1 algorithm. The algorithm used does not allow decryption, thus increasing the solution security.
- LDAP: Authenticates users in the SoftExpert Suite using the LDAP protocol connecting to the AD.
- SAML 2.0 (ADFS): Authenticates users in the SoftExpert Suite, with the user and password provided to the operating system, using the SAML protocol connected to the ADFS (Microsoft Active Directory Federation Service).
To increase security, SoftExpert Suite allows some security policies to be configured in the SoftExpert Configuration component. For example:
- Expire password: requires that the password is changed by the user;
- User blocking according to the number of attempts;
- Sending of e-mail to the manager when a user is blocked for exceeding the number of attempts;
- Strength control: requirement of a minimum or complexity size (presence of letters, numbers, symbols, and uppercases/lowercases) in passwords.
All requests are performed through the HTTPS protocol, which needs a logged and open section in the server to send an answer to the user. The session expiration time may be configured.
Access control
After the user logs in, SoftExpert Suite allows, through the access rights associated with each menu item, managing the access control of each resource individually through access right policies.
Solution
This topic contains details about the main security aspects in SoftExpert Suite access to the persistence layer and used services.
Database
SoftExpert Suite connects to the database by using basic authentication, through user name and password. The database connection configurations are stored in encrypted configuration files by using the SoftExpert Suite encryption algorithm.
E-mail
To send e-mail notifications, SoftExpert Suite is parameterized to connect to the e-mail server using basic authentication through user name and password, or OAuth authentication, through Microsoft or Google accounts. These data are stored in the database by means of the SoftExpert Suite encryption algorithm.
Directory
SoftExpert Suite may be configured to store documents in directories. For that, it is necessary to have permission to read and write to SoftExpert Suite (local user or domain user configured in IIS or NGinx) or for the File Manager Service, used only in remote directories. Users do not need to have access in these directories.
LDAP
To perform the LDAP service connection, either for authenticating or synchronizing the users data, SoftExpert Suite uses a valid AD user, entered in its parameterization. If using the LDAP synchronization and authentication functionality, make sure the rules to access the services in the company domain server are created in the firewall. The ports commonly used to make the connection with these services are listed below:
- 389/TCP
SAML
To authenticate users in SoftExpert Suite through the SAML protocol, make sure that the rules for access to the authentication and authorization services are created in the firewall. The ports commonly used for connection to these services are listed below:
- 443 TCP